Lifi: The New WireLess Tech
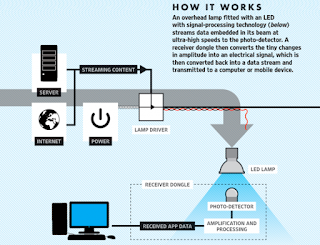
Imagine a world where every one of the billions of lightbulbs in use today is a wireless hotspot delivering connectivity at speeds that can only be dreamed of with Wi-Fi. That's the goal of the man who invented such a technology, and this week Li-Fi took a step out of the domain of science fiction and into the realm of the real when it was shown to deliver speeds 100 times faster than current Wi-Fi technology in actual tests. An Estonian startup called Velmenni used a Li-Fi-enabled lightbulb to transmit data at speeds as fast as 1 gigabit per second (Gbps), which is about 100 times faster than current Wi-Fi technology, meaning a high-definition film could be downloaded within seconds. The real-world test is the first to be carried out, but laboratory tests have shown theoretical speeds of 224 Gbps. Who Invented Li-Fi? The term was coined by German physicist Harald Haas during a TED Talk when he outlined the idea of using lightbulbs as wireless routers. That addre



