HTTP Response Splitting
The CRLF Injection Attack (sometimes also
referred to as HTTP Response Splitting) is a fairly simple, yet extremely
powerful web attack. Hackers are actively exploiting this web application
vulnerability to perform a large variety of attacks that include XSS cross-site
scripting, cross-user defacement, positioning of client’s web-cache, hijacking
of web pages, defacement and a myriad of other related attacks. A number
of years ago a number of CRLF injection vulnerabilities were also discovered in
Google’s Adwords web interface.
A simple
CRLF Injection example
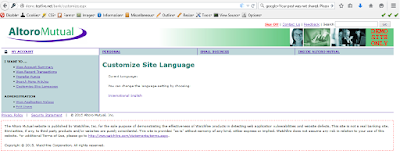
Suppose you run a vulnerable website that
has a language section. Sign in as admin and
goto customize site language option and select English as language and
intercept the request on proxy.
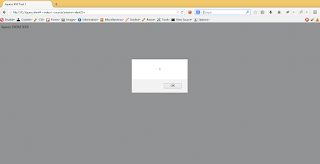
First response is actual response and
second response is our CRLF payload response due to which javascript executes,
XSS done
This attack appears to simply executes the script on the browser however the danger is that YOUR server has generated this HTML code, so effectively the hacker has injected HTML code into the victims browser via YOUR web server! Ouch. More sophisticated variations of this example can lead to poisioning of the client’s web-cache, cookies, XSS, temporary or permanent defacement of web pages and even information theft.
This attack appears to simply executes the script on the browser however the danger is that YOUR server has generated this HTML code, so effectively the hacker has injected HTML code into the victims browser via YOUR web server! Ouch. More sophisticated variations of this example can lead to poisioning of the client’s web-cache, cookies, XSS, temporary or permanent defacement of web pages and even information theft.





nice article
ReplyDeleteYeah Thanks!!
Delete