Snapdeal.com - Cross Site Scripting #Bug (DOM Based)
It was shocking to get
a XSS vulnerability in Snapdeal.com. Recently, I was using snapdeal for
purchasing for some goods but when i tried my luck for XSS, it was hardly a
matter of seconds.
Basically it was DOM
based XSS. The requested payload was not going to server. Instead it was being
include in DOM itself and executes on browser.
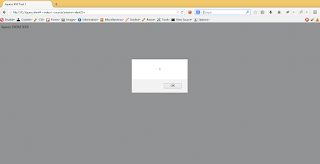
Proof of
Concept:
I used this URL with bcrumbSearch parameter which was used
for searching the product name from DOM.
As you
try to use this URL, script get executes on browser and I got a million dollar
smile.
Aftermath:
As a
responsible security researcher, I reported this issue to help@snapdeal.com and
support@snapdeal.com. I didn't got any reply from their side yet but meanwhile
issue got patched without any intimation.



Comments
Post a Comment